Here at Ice Moon Prison we bill by the second. Hence it is important that we always have the exact time. To this end, we are longtime users of the NTP Pool Project, a distributed network of Network Time Protocol-enabled servers around the world. As firm believers in paying one’s debt to society, Ice Moon Prison has joined the NTP Pool with one of its spare servers.
Since Ice Moon Prison is too cheap to have more than a single IPv4 address, and since we are IPv6 evangelists, the Ice Moon Prison NTP server is accessible over IPv6 only. Doing this is easier than messing around with NAT and port forwarding of UDP packets. (And, we might add, the following recipe is a testament to how easy setting up a service is without the burden of NAT. The same process can be followed for just about any service, not just NTP.)
Choose a server
Choosing a machine to run the NTP daemon is pretty simple. It needs to be always on; it needs to have a static IP address; it ought to be a physical, rather than a virtual, machine. Ice Moon Prison has a Mac mini running Ubuntu 13.04 that fits the bill.
The NTP Pool is, at its heart, a DNS server. Each time you query the address of pool.ntp.org, you get a different list of four servers. For this to work, the hosts must be at permanent, static, IP addresses. Fortunately, Ice Moon Prison’s ISP provides static IPv6 prefixes for everyone.
Assign an IPv6 address
Some operating systems have enabled IPv6 privacy extensions by default, which is reasonable enough for laptops and mobile devices, but counterproductive for servers. An NTP Pool host needs a static IP address, not a randomized one. We could have simply disabled IPv6 privacy extensions and used the stateless autoconfigured IPv6 address of the server based on its MAC address, but that would have to be changed if we switched the server’s hardware. We bit the bullet and set a completely static IPv6 address, one a little shorter and visually manageable.
Setting a static IPv6 address entails putting a section like this into the /etc/network/interfaces file:
iface eth0 inet6 static # Prefix 2001:44b8:41bd:c40x::/56 is from ISP. # Subnet xxxx:xxxx:xxxx:xxx1::/64 is from router. # Host part ::50 is chosen to be nice and short. address 2001:44b8:41bd:c401::50 # May as well still accept RFC 4862 router advertisements. accept_ra 1 autoconf 1 # Disable source address randomization. privext 0 netmask 64
Bring the interface down then up:
# ifdown eth0; ifup eth0
The IPv6 address should be present:
# ip -6 addr show eth0 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qlen 1000 inet6 fd30:a67b:b56:1:216:cbff:feab:43b0/64 scope global dynamic valid_lft forever preferred_lft forever inet6 2001:44b8:41bd:c401:216:cbff:feab:43b0/64 scope global dynamic valid_lft 86389sec preferred_lft 14389sec inet6 2001:44b8:41bd:c401::50/64 scope global valid_lft forever preferred_lft forever inet6 fe80::216:cbff:feab:43b0/64 scope link valid_lft forever preferred_lft forever
Configure the NTP daemon
NTP is installed by default on Ubuntu, but even on stock Debian it’s only a single apt-get command away:
# apt-get install ntp
The NTP Pool has recommendations for configuring a pool server, which basically boil down to: Don’t mention pool.ntp.org in your configuration, or you’ll cause positive feedback loops. So remove any existing server entries in /etc/ntp.conf and put in a few servers from their handy list:
server ntp.ragingfist.net server ntp.au.zoidial.com server ntp2.tpg.com.au server ntp.mazzanet.id.au server ntp.internode.on.net
Reload the NTP daemon configuration:
# service ntp reload
Open a hole in the firewall
Ice Moon Prison’s Mac mini is behind a firewall, so it is necessary to allow unsolicited UDP traffic on port 123 through the firewall. How to do this depends on the firewall. Ice Moon Prison runs OpenWrt 10.03.1, which uses the standard Linux iptables firewall. With OpenWrt’s LuCI interface this is pretty easy.
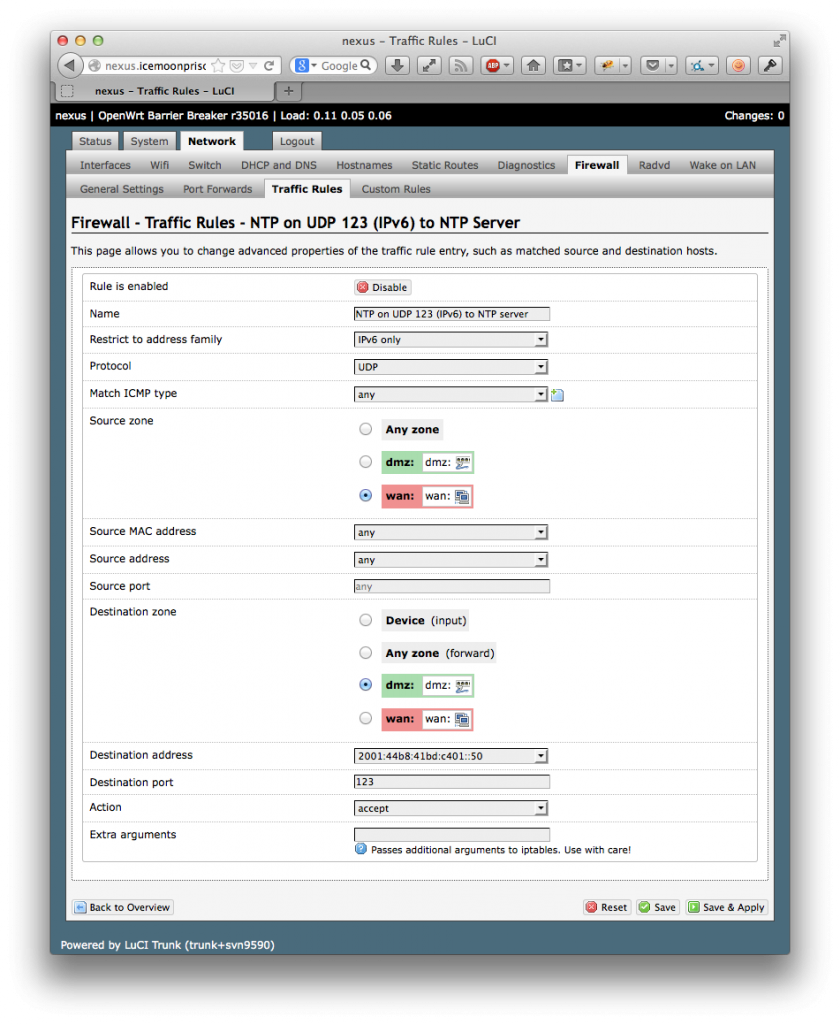
Register on pool.ntp.org
Registering your server’s IP address on pool.ntp.org is done through its home page. The NTP Pool provides a Statistics page for each server so you can see how yours is performing.
Leave a Reply